Senhasegura PAM
The Senhasegura Privileged Access Management solution is built to keep your business and its most valuable assets secure. Prevent malicious account or credential access with senhasegura.
Senhasegura's Privileged Access Management (PAM) solution provides comprehensive security for organizations by managing and controlling access to privileged accounts and sensitive information. It offers advanced features such as real-time monitoring, session recording, and threat detection to protect against unauthorized access and insider threats. Senhasegura PAM helps organizations achieve compliance with regulatory requirements and enhances overall security posture by ensuring that only authorized users have access to critical systems and data.
Key Benefits
- Best Value
Thanks to our straightforward pricing, easy deployment and management, and low resource requirements, we offer up to 70% lower Total Cost of Ownership (TCO) than competing solutions.
- Fastest Deployment
With our streamlined architecture, senhasegura PAM can be deployed in hours or days as opposed to weeks or months (or even years).
Our fast deployment provides fast time to security and value.
- Highest Customer Satisfactiont
We value customer service first and foremost, and our users vouch for it.
We have the highest customer satisfaction rating and user recommendation rate in the industry on Gartner Peer Insights and senhasegura is the only PAM vendor to have a full 5-star customer satisfaction rating.
- Unparalleled User Experience
Let’s face it, if a security solution creates friction and slows users down, they’ll find a way to get around it.
senhasegura PAM provides a top-tier user experience for both end users and admins, reducing friction and improving efficiency.
- Highest Security
Our solution has been meticulously architected and developed to offer the highest possible security. senhasegura PAM has been tested and certified time and time again to make sure your most valuable digital assets are in good hands.
- Future-Proof Architecture
We have invested in modern architecture and development practices to give you a future-proof solution that scales and evolves with your needs and adapts in the ever-changing threat landscape.
- No Hidden Costs
We offer a full-stack, plug-and-play platform with no hidden or additional costs. Our all-inclusive pricing means no surprise fees, just clear-cut benefits. Also, depending on your needs, you can select perpetual license or subscription pricing.
- Easy upgrades, less downtime
senhasegura’s stable, all-in-one platform offers built-in High Availability (HA) and Disaster Recovery (DR) capabilities, ensuring seamless upgrades and recovery from disasters with minimum downtime.
Every customer environment is different, so you have the freedom to deploy our PAM solution in the way that best suits your needs, whether it’s through a SaaS, private cloud, hybrid cloud, or on-premises solution. Regardless of how you deploy, you get the same great features, usability, and value.
Features
Senhasegura is the only PAM solution available on the market that covers the entire privileged access lifecycle.
- Secure Vault and Password Manager: Takes highly privileged administrative accounts and passwords out of the direct control of users and stores them securely in a software vault that regularly rotates passwords based on your policies.
- SSH Key Management: Manages trust relationships between SSH keys and systems. Controls and traces SSH key use.
- Enhanced Auditing, Reporting, and Compliance: Records every session within the system, ensuring comprehensive tracking of all actions. This robust auditing capability allows users to quickly find the cause of any cyber incident and meet compliance demands.
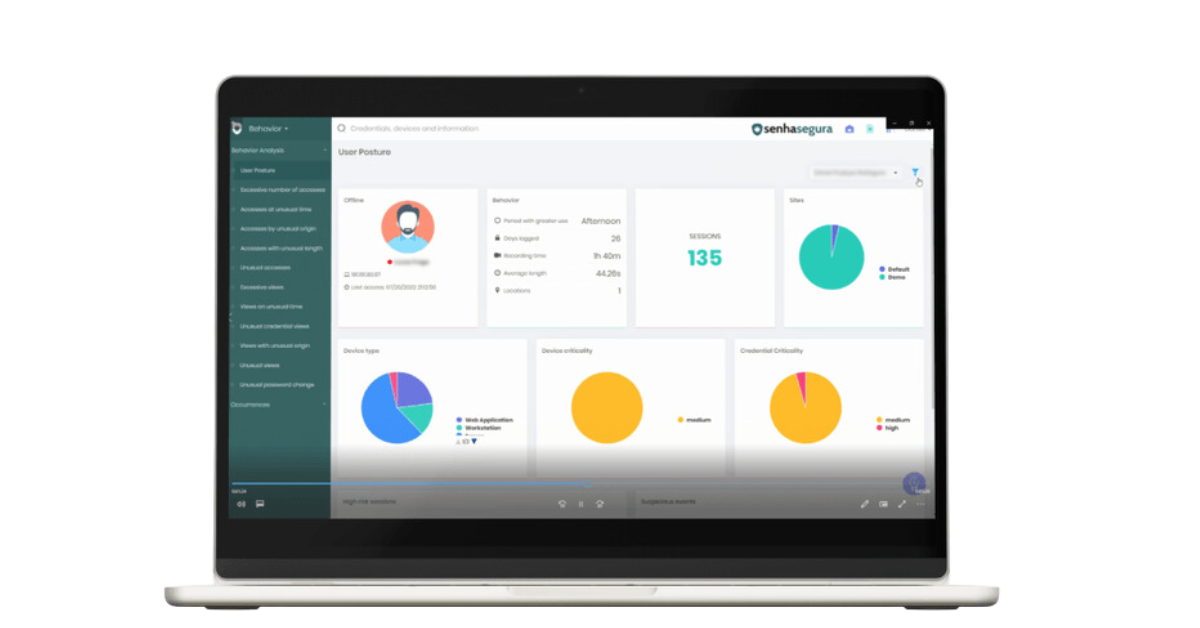
- Behavioral Analysis: Identifies and responds to any change in behavior patterns and user access profiles.
- Session Monitoring, Recording, and Control: Monitors user activities and detects suspicious events in real-time, including the possibility of pausing or ending the user’s session simply and quickly. Records sessions for forensics and auditing. We offer better performance delivering up to 7 times more video storage capacity than competing solutions.
- Automation: Automates routine workflows to decrease the workload of your IT and security staff and reduce user friction.
- Approval Workflows: Implements multilevel approval flows and validation provided by the requesting user on remote sessions or password-viewing cases, with alerts via email or SMS.
- Granular Acces Control: Provides and revokes privileges for local user access on Windows, Linux, Unix, Databases, and Active Directory platforms without the need to install anything on the target device.
- Account and Discovery: Seamlessly maps and identifies all of the environment’s connected assets, including their credentials and digital certificates. This offers comprehensive integration for devices, legacy applications, credentials, containers, playbooks, and SSH keys.
- Service Account Governance: Secures and controls your service accounts, removing passwords from the hands of your users and automatically changing service account passwords on a regular basis.
- Visual Dashboards: Updates the interactive dashboards with real-time insights into the security configurations and privileged access activities across your infrastructure. The dashboards can also be used to identify and mitigate any risky behavior instantly.
- Scripting and Integrations: Integrated and fully supported macro tools for multiple protocols (SSH, RDP...) and APIs. Seamless compatibility across operating systems, web applications, network and security devices, virtualization environments, databases, directory systems, remote access and monitoring tools, as well as mobile devices and browsers.
- Multi-Factor Authentication: Validates privileged users with secure Multi-Factor Authentication and secures access to business resources with Single Sign-On.
- Database Proxy: Streamlines your database management with integrated PAM features to guarantee secure operation. Administrators have the power to enable, monitor, and restrict operations. Users can use their preferred client to access databases directly from their workstations without the need for passwords. This cutting-edge feature also includes a pioneering command filter for Oracle.